USA / Canada 866-503-1471
International +972-722-405-222
HashiCorp Vault - Open Source & Enterprise
Vault הוא כלי המנהל, מאחסן ומגן על מידע רגיש בדרך המצמצמת התפזרות של סודות ובצורה המאפשרות לארגונים גדולים לתפעל זאת בנוחות - וגם בכמויות מידע גדולות.
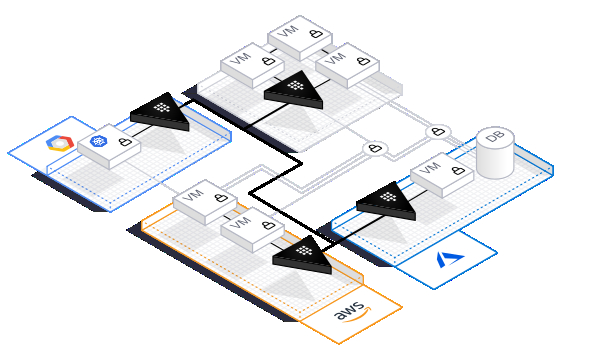
בעולם שבו מידע סודי מופץ בצורה גלובלית, העניין קריטי במיוחד כאשר פורסים את התשתיות על פני עננים רבים (ציבוריים ופרטיים).
ניתן לראות את Vault גם ככלי המספק למעשה כספת מרכזית לארגון.
Vault מספק את היכולות הבאות:
- הגנה על גישה לטוקנים, סיסמאות, תעודות סרטפיקציה, מפתחות הצפנה
- ניהול סודות (כולל סודות דינאמיים הנוצרים on-demand וזמינים לזמן קצר)
- הגנה ואחסנה של מידע רגיש
- ממשק UI גרפי
- ממשק CLI (גם לצורכי אוטומציה)
- API עשיר מבוסס HTTP ו- REST
- הצפנה כשירות - הצפנת מידע אפליקטיבי
- יכולות הגדרת מדיניות לבקרת גישה (ACL)
- גישה מבוססות זהויות
- לוגים מלאים ו- Audit Trail
- התקנה פנים-ארגונית (on-premises), בענן ציבורי או בענן פרטי
- אינטגרציה עם העננים המובילים: Amazon (AWS), Azure, Google Cloud (GCP)
- התוכנה ניתנת להתקנה עצמית על Windows, Mac OS X, Linux, FreeBSD, OpenBSD, Solaris
- יכולות מתקדמות של Multi-Dacacenter - לצרכי DR , HA ורפליקציה
- יכולת Policy as code framework באמצעות המוצר Hashicorp Sentinel (בגירסת Premium בלבד)
היכרות עם Vault - מועבר ע"י מייסד HashiCorp (זמן צפיה: 16 דקות)
היתרונות ב- Vault
- המערכת כתובה בקוד פתוח: הדבר מאפשר שליטה מלאה על המערכת (אפשר לשנות ולקסטם בהתאם לצרכים המדוייקים שלך), וכן אפשר לראות את השיחות סביב רכיבי המערכת, להשתתף בדיונים עליהם ולהשפיע!
הדבר גם מסייע לפיתוח מהיר יותר של המערכת - המוצר מספק אבטחה המותאמת לארכיטקטורת Microservices . למידע נוסף לחצו כאן.
- תמיכה מלאה ב- High Availability למערכות קריטיות
- מערכת שתומכת גם ב- scale גדול מאוד
- יכול לעבוד עם כל כלי Configuration Management (כגון Chef, Puppet, Ansible ועוד)
- כל המידע נרשם ללוג – ופעולה תכשל אם לא ניתן לרשום ללוג
- מערכת נוחה למפתחים - מפתחים ישמחו לעבוד מול ה- API של המערכת (ולקבל בקלות Encryption as a Service)
- אינטגרציות מובנות עם כלים מובילים רבים: ניתן לחבר את המערכת בקלות לכלים משלימים, כגון JIRA, Jenkins, Docker, Kubernetes, Visual Studio, Eclipse, IntelliJ ועוד
- מותאם לרגולציות GDPR ורגולציות נוספות
איך נוכל לעזור לך?






חברת ALM-Toolbox היא המפיצה הרשמית של Vault ומוצרי HashiCorp בישראל (ובמדינות נוספות), ומתמחה גם במתן שירותים נוספים ל- Vault , וביניהם:
- תכנון מערכת Vault והטמעתה בשרתי הארגון, בענן פרטי או ציבורי (דוגמת AWS, Azure, Google Cloud ועוד)
- סיוע בהתאמה בין תהליכי הפיתוח וה- production בארגון לבין התהליכים המוצעים ב- Vault
- אינטגרציה לכלים משלימים, דוגמת Terraform, Consul, Kubernetes, Nomad, Sentinel, git, GitLab, Chef, Puppet, Jenkins, Spotinst, Docker, Artifactory ועוד
- שירותים מנוהלים (managed services) ומרכז תמיכה - כולל אפשרות ל- SLA - גם לתקופות קצרות. למידע נוסף לחצו כאן
- פיתוח אינטגרציות ותוספות מותאמות לצרכי הלקוח (כגון דו"חות מותאמים)
- הדרכות
- מיגרציה אל Vault ומיגרציה מכלים דומים
- יעוץ לגבי רישוי ומכירת רשיונות Enterprise (ענן ו- on-premises)
פיצ'רים ורישוי Vault Enterprise Pricing - טבלת השוואה
הטבלה להלן מכילה מידע חלקי בלבד. לקבלת טבלת Excel מפורטת לכל המודולים עם אפשרויות סינון ומיון נוחות ומתקדמות - כתבו לנו ונשלח לכם במייל
| Feature |
Open SourceSecrets management and data protection |
EnterpriseCollaboration and operations features; Multi-datacenter, Scale, Governance and Policy features for organizations לחצו להצעת מחיר |
|
|---|---|---|---|
| CUSTOMER SUPPROT & SLA | |||
|
Support
|
- | ||
| SECRETS MANAGEMENT | |||
|
Dynamic Secrets
Dynamic secrets are generated on demand and are unique to a client and can be revoked immediately after use, minimizing the life of the secret
|
|||
|
Secret Storage
Encrypt data while at rest, in the storage backend of your choice
|
|||
|
Secure Plugins
Improve the extensibility of Vault with pluggable backends
|
|||
|
Detailed Audit Logs
Vault stores a detailed audit log of all authenticated client interaction (authentication, token creation, secret access, secret revocation, etc.)
|
|||
|
Leasing & Revoking Secrets
Manage authorization tokens throughout your infrastructure: Create time-based tokens for automatic revocation or manual revocation
|
|||
|
ACL Templates
Support templating for identity groups, entities, and metadata within ACL policies
|
|||
|
Vault Agent
Automatically manage the secure introduction and renewal of tokens for local applications
|
|||
|
Init & Unseal Workflow
Web browser accessible workflow
|
|||
|
Key Rolling
Key Rolling allows the ability to update and roll new keys throughout distributed infrastructure while retaining the ability to decrypt values encrypted with past key versions
|
|||
|
UI with Cluster Management
Perform all CLI/API actions from one easily accessible browser interface for secret administration and Vault multi-datacenter cluster management
|
|||
|
Entities & Identity Groups
An integrated system for understanding the identity of a person or system across their logins and tokens and using this information for policy and access control decisions
|
|||
|
Access Control Policies
Create and manage policies that authorize access control throughout your infrastructure and organization
|
|||
|
Identity Plugins
Extend Vault with pluggable authentication methods to directly integrate with your trusted identity providers
|
|||
|
Integrated Storage
Securely store persistent data in Vault without an external storage backend. Integrated Storage supports High Availability and Replication
|
|||
|
Rate Limit Quotas
Limit maximum amount of requests per second (RPS) to a system or mount to protect network bandwidth
|
|||
| Data Protection | |||
|
Encryption as a Service
Encrypt application data during transit and at rest.
| |||
|
Transit Backend
Encrypt and decrypt application data with a HTTP (TLS) API call. Key management, encryption algorithm, and more are offloaded and centrally managed by Vault.
| |||
|
Encryption Key Rolling
Encryption key rolling.
| |||
| Identity-based Access | |||
|
Entities & identity groups
An integrated system for understanding the identity of a person or system across their logins and tokens and using this information for policy and access control decisions.
| |||
|
Access Control Policies
Create and manage policies that authorize access control throughout your infrastructure and organization.
| |||
|
Identity plugins
Identity plugins.
| |||
|
AWS KMS Auto-unseal
Automatically unseal Vault clusters using AWS Key Management System.
| |||
|
Azure Key Vault Auto-Unseal
Automatically unseal Vault clusters using Azure Key Vault System.
| |||
|
GCP Cloud KMS Auto-unseal
Automatically unseal Vault clusters using GCP Cloud Key Management System.
| |||
| ENTERPRISE PLATFORM | |||
|
Disaster Recovery
Failover Vault clusters from one data center to another with limited downtime.
| - | ||
|
Namespaces
Provide Secure Multi-tenancy within Vault via isolated, self-managed environments.
| - | ||
|
Monitoring
Monitor Vault telemetry and log data with Splunk
| - | ||
| Multi-DataCenter Module | |||
|
Replication
Replication provides high availability replication of secrets and policies across multiple data centers and clouds and is built around global deployments of Vault.
| - | ||
|
Replication Filters
Selectively whitelist/blacklist and activate or deactivate mounts for Secret Mounts for Replication.
| - | ||
|
Read Replicas
Multiply read performance for Vault Enterprise infrastructure via a new type of performance-focused node within Vault to speed up read performance within a single cluster. This is particularly useful for clusters with a high amount of throughput.
| - | ||
|
Path Filters
Path filters allow for mounts within namespaces to be filtered similar to existing mount filters, allowing for namespace admins to specify what secrets within a namespace will be omitted from performance replication
| - | ||
| Governance & Compliance Module | |||
|
Control Groups
Require multiple Identity Entities or members of Identity Groups to authorize an requested action before it is allowed to run.
| - | ||
|
HSM Auto-unseal
Vault integrates HSM Master Key Wrapping and Automatic Unsealing for HSM installations.
| - | ||
|
Multi-factor Authentication
Enforce MFA workflows when accessing a secret or a secret path.
| - | ||
|
Sentinel Integration
Take advantage of HashiCorp Sentinel to provide extremely flexible access control policies -- even on unauthenticated endpoints.
| - | ||
|
FIPS 140-2 & Seal Wrap
Vault can take advantage of FIPS 140-2-certified HSMs to ensure that Critical Security Parameters are protected in a compliant fashion.
| - | ||
|
Entropy Augmentation
Entropy Augmentation","description":"Entropy Augmentation allows Vault Enterprise to sample entropy (or randomness for cryptographic operations) from an external source via the seals interface
| - | ||
|
Lease Count Quotas
Limit the number of leases generated in a system or mount to protect system stability and storage performance at scale
| - | ||
| Advanced Data Protection Module | |||
|
KMIP
Integrate with trusted enterprise databases and workloads via KMIP protocol
| - | ||
|
Transform
A powerful new way to protect sensitive data (SSN, PII, PCI, credit cards, etc), data structure, and masking across clouds, applications, and systems","offeredIn
| - | ||
| CUSTOMER SUPPROT & SLA | |||
|
Support
|
- | ||
| Pricing | Free | לחצו להצעת מחיר | |
הטבלה להלן מכילה מידע חלקי בלבד. לקבלת טבלת Excel מפורטת לכל המודולים עם אפשרויות סינון ומיון נוחות ומתקדמות - כתבו לנו ונשלח לכם במייל
המלצות על Vault
Vault Enterprise has been pivotal in how we've deployed some of our architecture
 Tyler Haley, Cloud Service Provider Lead, US Department of Defense
Tyler Haley, Cloud Service Provider Lead, US Department of Defense
Our developers at Adobe found HashiCorp Vault to be "head and shoulders" above anything else we tested
 Chandler Allphin, Lead Security Engineer, Adobe
Chandler Allphin, Lead Security Engineer, Adobe
Using keys with Vault Enterprise is the most secure way we could found
 Nir Koren, DevOps CI/CD Team Leader, LivePerson
Nir Koren, DevOps CI/CD Team Leader, LivePerson