USA / Canada 866-503-1471
International +972-722-405-222
Akeyless Vault Platform
Akeyless is a unified Vault platform built to secure credentials and access to production resources across hybrid cloud and legacy environments.
Akeyless offers two solutions:
- Akeyless Vault for Secrets Management: Protect and automate access to secrets like credentials, keys, tokens, and API-Keys across your DevOps tools and Cloud platforms using a secured vault
- Secure Remote Access: Access any system from anywhere based on user identity. Secure your infrastructure and applications by enabling a unified authentication and ephemeral just-in-time access permissions with Akeyless Secure Remote Access
Vault for Secrets Management
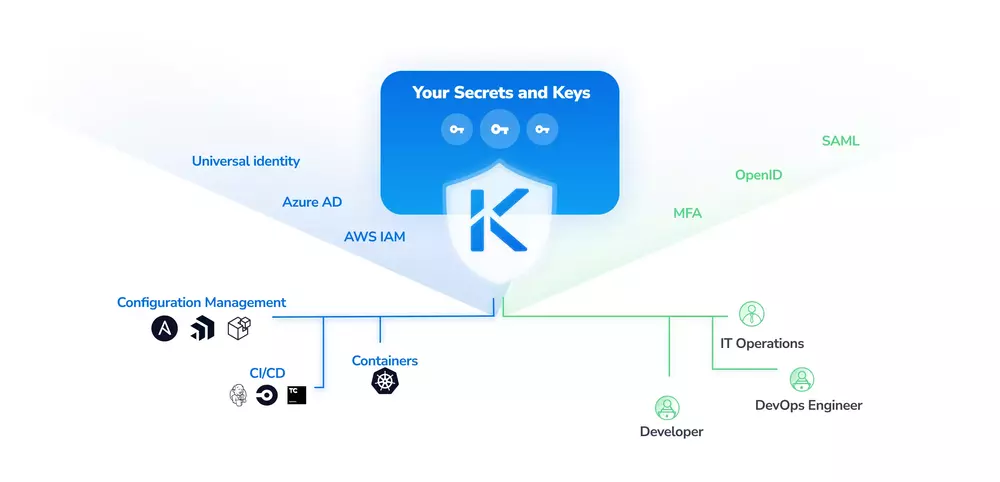
Akeyless provides the following:
- Static and dynamic secrets
- Just-in-time Secrets: Ephemeral secrets & access permissions are generated on-demand
- Wipeout API-Keys & Tokens: Eliminate credentials and passwords from DevOps tools, scripts, and source code, using CLI, SDKs and native plugins
- Eliminate SSH Keys: Provide SSH access via short-lived certificates, without the need for ssh pairs
- PKI Certificates Automation: Automatically issue and renew short-lived certificates rather than long-lived certs
- UI and CLI interfaces
- Full Key Life Cycle Management
- Multi Cloud KMS: Provision and enhance your control of encryption keys across cloud providers KMS
- Encryption-as-a-Service: Encrypt and decrypt application data with a simple API call
- Storage-Level Encryption with KMIP: Unify encryption processes by connecting databases and storage devices, including MongoDB, VMware ESX and more
- Encrypted Key/Value Store: Protect any type of secret like connection strings, passwords, tokens and encryption keys with Zero-Knowledge Encryption
- Integrate your DevOps: use secrets in your CI/CD pipelines, Configuration Management, and Container Orchestration tools
- Integrate into your Code: Eliminate secret proliferation in code by using various SDKs
- Password Management for Teams: Enable humans to also manage secrets via a browser extension (Chrome and Firefox), providing quick access to private and teams shared secrets
- Granular Machine Identities: Segregate access between identities at various levels (i.e. pods, namespaces, playbooks, jobs and more)
- Least Privileges: Limit machines and users’ access rights, to the minimum they need
- Log Usage & Audit trail
- Integrate with SIEM: Empower the analysis of your logs by shipping them to a central SIEM or your log management system
- Analytics & Insights
SECRET MANAGEMENT:
CENTRALLY MANAGE ENCRYPTION:
SEAMLESSLY CONNECT TO YOUR STACK:
AUDIT & COMPLIANCE:
Watch Akeyless Vault Overview (5 min.)
Akeyless' Benefits
- SaaS (cloud) or hybrid gives you full control and easy deployment so you can start instantly
- Zero Knowledge of your secrets and keys : That encryption technoolgoy makes sure that nobody, not even your cloud service provider, can access the most sensitive data in your organization
- Affordable and transparent pricing saves you money
- Built for multi-cloud so it helps you avoid vendor lock-in
- Scale seamlessly so you don't have to worry about complex infrastructure when you scale up
- Improve your security posture
- Reduce secrets sprawl and exposure risks
- Managed service (SaaS - Software as a Service)
- Cloud solution you can also enjoy on-premises using a gateway
- Gain compliance
Pricing
Pricing starts at $40 / month for 4 clients and 50 secrets. Free edition is also possible.Contact us for quotes and inquiries: akeyless@almtoolbox.com or +972-722-405-222 / 866-503-1471 (USA & Canada)
How We Can Help You







We've been partnered with Akeyless company and we have experts that can help you with the following:
- Implement integration with your DevOps flows, CI/CD pipelines and business workflows
- Plan migration from HashiCorp Vault, AWS Secret Management and more
- Running POC / Demo / trial
- We can help you with purchasing and managing licenses
- Comparing Akeyless with similar tools such as HashiCorp Vault and AWS
- Training
News & Related Articles
Testimonials and Customers Stories
People here really like the Akeyless Vault service - they find it easy and better than our previous service, and we get Akeyless in lowered costs"
 Dr. Conor Mancone, Lead Application Security Engineer, Cimpress Cimpress
Dr. Conor Mancone, Lead Application Security Engineer, Cimpress Cimpress
Akeyless is a true software as a service, which means zero maintenance for me. It offers a strong encryption model ... and we found that to have a much lower cost of ownership and deployment was much quicker."
 Chris Holden, CISO, Crum & Forster
Chris Holden, CISO, Crum & Forster
Distributed Fragment Cryptography technology by Akeyless, makes sure that encryption keys are never kept as whole, and never in one-party hands, eliminating the necessity to trust the service provider with your keys."
 Oran Holander, CISO, Babylon Health
Oran Holander, CISO, Babylon Health
Akeyless’ innovative key management technology meets the newest needs of hybrid and multi-cloud cryptographic operations, which ensures a more effective data protection implementation, and meets key regulatory requirements as of today."
 Nir Chervoni, Head of Data Security, Booking.com
Nir Chervoni, Head of Data Security, Booking.com
By providing frictionless Zero Trust Access via a unified authentication and just-in-time access, Akeyless positions itself as a true PAM 2.0 offering, eradicating the shortcomings of the traditional PAM solutions."
 Ramy Houssaini, Chief Cyber & Tech Risk, BNP Paribas
Ramy Houssaini, Chief Cyber & Tech Risk, BNP Paribas
Akeyless introduces a unique and innovative approach for Secrets Management… The SaaS availability, ease of use, seamless integration, and security capabilities - with Zero-Trust Encryption - made Akeyless our selected solution."
 Shay Fainberg, Chief Information Security Officer, Outbrain
Shay Fainberg, Chief Information Security Officer, Outbrain
Akeyless offers the balance of not only do what we have to solve the Secure Remote Access component; we have to solve secrets management. That is a problem that we also were dealing with and we like the ability to have that in one solution. You can manage all of your identities both human and machine in one place"
 Gavin Grisamore, CISO, Stash
Gavin Grisamore, CISO, Stash