France  01 84 17 53 28
01 84 17 53 28
International +972-722-405-222
HashiCorp Vault - Open Source & Enterprise
Vault est un outil qui gère, stocke et protège les informations sensibles d'une manière qui réduit la propagation des secrets et d'une manière qui permet aux grandes organisations de les exploiter confortablement et ce également pour de grandes quantités d'informations.
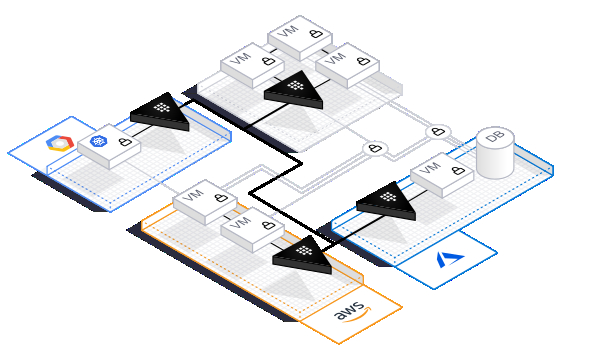
Dans un monde où les informations confidentielles sont distribuées de manière globale, cela est particulièrement critique lors du déploiement d'une infrastructure sur plusieurs clouds (publics et privés).
Vault peut également être considéré comme un outil qui fait office de coffre-fort central pour l'organisation.
Vault offre les fonctionnalités suivantes:
- Protéger l'accès aux jetons, mots de passe, certificats, clés de chiffrement
- Sécurisation des secrets (y compris les secrets dynamiques créés à la demande et disponibles pendant une courte période)
- Protection et stockage des informations sensibles
- Interface utilisateur graphique
- Interface CLI (également à des fins d'automatisation)
- API riche basé sur HTTP et REST
- Cryptage en tant que service - cryptage des informations applicatives
- Possibilité de configuration de la stratégie de contrôle d'accès (ACL)
- Approche basée sur l'identité
- Log d’activité et Audit Trail
- Installation sur site, dans un cloud public ou dans un cloud privé
- Intégration avec les principaux clouds: Amazon (AWS), Azure, Google Cloud (GCP)
- Le logiciel peut être auto-installé sur Windows, Mac OS X, Linux, FreeBSD, OpenBSD, Solaris
- Capacités avancées Multi-Dacacenter - pour les besoins de DR, HA et de réplication
- Possibilité de définir une stratégie en tant que cadre de code à l'aide du produit
- Hashicorp Sentinel (version Premium uniquement)
Introduction à Vault - présenté par le fondateur de HashiCorp (durée de la vidéo : 16 minutes)
Les avantages de Vault
- Le système est écrit en open source : cela permet un contrôle total du système (vous pouvez le modifier et le personnaliser en fonction de vos besoins exacts) et vous pouvez voir les conversations autour des composants du système, participer aux discussions à leur sujet et influencer , cela contribue également à un développement plus rapide du système
- Support total "High Availability" pour les systèmes critiques
- Compatible avec n'importe quel outil Configuration Management (tel que Chef, Puppet, Ansible et autres)
- Toutes les informations sont enregistrées - et l’opération échouera s'il n'est pas possible de se connecter
- Kit de développement pratique - Les développeurs seront heureux de travailler avec l'API système (et d'obtenir facilement Encryption as a service)
- Intégrations intégrées avec de nombreux outils de pointe: le système peut être facilement connecté à des outils complémentaires, tels que JIRA, Jenkins, Docker, Kubernetes, Visual Studio, Eclipse, IntelliJ et plus
- Adapté aux réglementations GDPR et d’autres règlementations
Comment pouvons nous vous aider ?






-
ALMtoolbox est le distributeur officiel des produits Vault et HashiCorp en France (et dans d'autres pays), et se spécialise également dans la fourniture de services supplémentaires à Vault, notamment:
- Concevoir de système Vault et l'implémenter dans les serveurs de l'organisation, dans un cloud privé ou public (comme AWS, Azure, Google Cloud et plus)
- Aide à faire correspondre les processus de développement et de production dans l'organisation avec les processus offerts dans Vault
- Intégration avec des outils complémentaires, tels que Terraform, Consul, Kubernetes, Nomad, Sentinel, git, GitLab, Chef, Puppet, Jenkins, Spotinst, Docker, Artifactory et plus Services gérés et centre de support - y compris la possibilité de SLA - même pour de courtes périodes.
- Développement et intégration et de modules complémentaires adaptés aux besoins du client (tels que des rapports personnalisés)
- Formations
- Migration vers Vault et migration à partir d’outils similaires
- Conseil en matière de licences et de vente de licences d'entreprise (cloud et sur site) Vous pouvez nous contacter par email ou par téléphone (+33 184 17 53 28) pour coordonner une démonstration et recevoir une offre commerciale
Nouvelles et article
Dans notre blog en français appuyez Vault pour accéder à toutes les mises à jourTarification des fonctionnalités et des licences d'entreprise - Tableau de comparaison
Pour recevoir le tableau Excel de toits les fonctionalites par model ecrive nous et nous enverrons ce tableau detaille, le tableau ci-dessous presente une synthese Ecrivez nous nous vous enverrons un mail
| Feature |
Open SourceSecrets management and data protection |
EnterpriseCollaboration and operations features; Multi-datacenter, Scale, Governance and Policy features for organizations Pour un devis |
|
|---|---|---|---|
| CUSTOMER SUPPROT & SLA | |||
|
Support
|
- | ||
| SECRETS MANAGEMENT | |||
|
Dynamic Secrets
Dynamic secrets are generated on demand and are unique to a client and can be revoked immediately after use, minimizing the life of the secret
|
|||
|
Secret Storage
Encrypt data while at rest, in the storage backend of your choice
|
|||
|
Secure Plugins
Improve the extensibility of Vault with pluggable backends
|
|||
|
Detailed Audit Logs
Vault stores a detailed audit log of all authenticated client interaction (authentication, token creation, secret access, secret revocation, etc.)
|
|||
|
Leasing & Revoking Secrets
Manage authorization tokens throughout your infrastructure: Create time-based tokens for automatic revocation or manual revocation
|
|||
|
ACL Templates
Support templating for identity groups, entities, and metadata within ACL policies
|
|||
|
Vault Agent
Automatically manage the secure introduction and renewal of tokens for local applications
|
|||
|
Init & Unseal Workflow
Web browser accessible workflow
|
|||
|
Key Rolling
Key Rolling allows the ability to update and roll new keys throughout distributed infrastructure while retaining the ability to decrypt values encrypted with past key versions
|
|||
|
UI with Cluster Management
Perform all CLI/API actions from one easily accessible browser interface for secret administration and Vault multi-datacenter cluster management
|
|||
|
Entities & Identity Groups
An integrated system for understanding the identity of a person or system across their logins and tokens and using this information for policy and access control decisions
|
|||
|
Access Control Policies
Create and manage policies that authorize access control throughout your infrastructure and organization
|
|||
|
Identity Plugins
Extend Vault with pluggable authentication methods to directly integrate with your trusted identity providers
|
|||
|
Integrated Storage
Securely store persistent data in Vault without an external storage backend. Integrated Storage supports High Availability and Replication
|
|||
|
Rate Limit Quotas
Limit maximum amount of requests per second (RPS) to a system or mount to protect network bandwidth
|
|||
| Data Protection | |||
|
Encryption as a Service
Encrypt application data during transit and at rest.
| |||
|
Transit Backend
Encrypt and decrypt application data with a HTTP (TLS) API call. Key management, encryption algorithm, and more are offloaded and centrally managed by Vault.
| |||
|
Encryption Key Rolling
Encryption key rolling.
| |||
| Identity-based Access | |||
|
Entities & identity groups
An integrated system for understanding the identity of a person or system across their logins and tokens and using this information for policy and access control decisions.
| |||
|
Access Control Policies
Create and manage policies that authorize access control throughout your infrastructure and organization.
| |||
|
Identity plugins
Identity plugins.
| |||
|
AWS KMS Auto-unseal
Automatically unseal Vault clusters using AWS Key Management System.
| |||
|
Azure Key Vault Auto-Unseal
Automatically unseal Vault clusters using Azure Key Vault System.
| |||
|
GCP Cloud KMS Auto-unseal
Automatically unseal Vault clusters using GCP Cloud Key Management System.
| |||
| ENTERPRISE PLATFORM | |||
|
Disaster Recovery
Failover Vault clusters from one data center to another with limited downtime.
| - | ||
|
Namespaces
Provide Secure Multi-tenancy within Vault via isolated, self-managed environments.
| - | ||
|
Monitoring
Monitor Vault telemetry and log data with Splunk
| - | ||
| Multi-DataCenter Module | |||
|
Replication
Replication provides high availability replication of secrets and policies across multiple data centers and clouds and is built around global deployments of Vault.
| - | ||
|
Replication Filters
Selectively whitelist/blacklist and activate or deactivate mounts for Secret Mounts for Replication.
| - | ||
|
Read Replicas
Multiply read performance for Vault Enterprise infrastructure via a new type of performance-focused node within Vault to speed up read performance within a single cluster. This is particularly useful for clusters with a high amount of throughput.
| - | ||
|
Path Filters
Path filters allow for mounts within namespaces to be filtered similar to existing mount filters, allowing for namespace admins to specify what secrets within a namespace will be omitted from performance replication
| - | ||
| Governance & Compliance Module | |||
|
Control Groups
Require multiple Identity Entities or members of Identity Groups to authorize an requested action before it is allowed to run.
| - | ||
|
HSM Auto-unseal
Vault integrates HSM Master Key Wrapping and Automatic Unsealing for HSM installations.
| - | ||
|
Multi-factor Authentication
Enforce MFA workflows when accessing a secret or a secret path.
| - | ||
|
Sentinel Integration
Take advantage of HashiCorp Sentinel to provide extremely flexible access control policies -- even on unauthenticated endpoints.
| - | ||
|
FIPS 140-2 & Seal Wrap
Vault can take advantage of FIPS 140-2-certified HSMs to ensure that Critical Security Parameters are protected in a compliant fashion.
| - | ||
|
Entropy Augmentation
Entropy Augmentation","description":"Entropy Augmentation allows Vault Enterprise to sample entropy (or randomness for cryptographic operations) from an external source via the seals interface
| - | ||
|
Lease Count Quotas
Limit the number of leases generated in a system or mount to protect system stability and storage performance at scale
| - | ||
| Advanced Data Protection Module | |||
|
KMIP
Integrate with trusted enterprise databases and workloads via KMIP protocol
| - | ||
|
Transform
A powerful new way to protect sensitive data (SSN, PII, PCI, credit cards, etc), data structure, and masking across clouds, applications, and systems","offeredIn
| - | ||
| CUSTOMER SUPPROT & SLA | |||
|
Support
|
- | ||
| Pricing | Free | Pour un devis | |
Pour recevoir le tableau Excel de toits les fonctionalites par model écrivez nous et nous enverrons ce tableau detaille, le tableau ci-dessous presente une synthese - Ecrivez nous nous vous enverrons un mail
Recommendations sur Vault
Vault Enterprise has been pivotal in how we've deployed some of our architecture
 Tyler Haley, Cloud Service Provider Lead, US Department of Defense
Tyler Haley, Cloud Service Provider Lead, US Department of Defense
Our developers at Adobe found HashiCorp Vault to be "head and shoulders" above anything else we tested
 Chandler Allphin, Lead Security Engineer, Adobe
Chandler Allphin, Lead Security Engineer, Adobe
Using keys with Vault Enterprise is the most secure way we could found
 Nir Koren, DevOps CI/CD Team Leader, LivePerson
Nir Koren, DevOps CI/CD Team Leader, LivePerson