To encourage downloads of the ‘Shield’ app that fights coronavirus, we have built a complementary Continuous Integration (CI) solution and code scanners to improve information security, code security and privacy of the app. We also invite the developers to use it freely and continuously in future.
A few days ago, the Israeli Ministry of Health released “The Shield” application – which tells you when you’ve come in contact with a coronavirus patient, determined via cross-location of the mobile phone owner against known locations’ of Corona patients (see link in the bottom for more information on how it works).
This is an important app that has also received the blessing of the open source community.
The app has been downloaded about a million times so far – but it’s still not enough (the more downloads, the more people will get real-time updates about their exposure to verified patients).
Reading the comments on the internet, I saw that of the intended user audience, many were still a bit suspicious of the app.
We (ALM-Toolbox company) brainstormed how we could help increase trust in the app and contribute to increasing the amount of downloads – and we saw that there was no automatic code scan of the code.
Such a scan can reveal security and privacy breaches, and increase trust in the app (and hopefully – also contribute to its additional downloads)
That’s why we decided to set up a complementary CI solution that includes code scanning and finding security breaches.
We decided to use GitLab for the following reasons:
- The tool allows you to run a collection of code scans for security aspects and to detect vulnerabilities (especially for React – the language in which the app was written)
- Since this is open source, we decided to use the CI tool, which itself is open-source
- We’re experienced in this tool (from previous projects we have carried out as well as representing the GitLab company for years)
- Using all the security tools is free for public projects – so we can also let more people join and contribute to the project
- It can be connected to a project on GitHub (since both have a shared git base)
- The CI is accessible in the cloud so we can easily attach additional donors to the project without the need for additional tools
Over the past few days we have spent several hours studying the application and building a CI (Continuous Integration) solution tailored to the app and the code languages it was written and built into.
So what did we apply?
- Static code scan (SAST) running on the application code
- Scan Dependencies to detect bad packages usage
- Security reports (collected into a useful dashboard)
- Container Scanning (for the CI module we made as we used Docker containers to run the scanning)
- Connects the project on GitHub with the CI, so that a new pipeline runs every time a push is made to the app code (usually adding new code or updating the code)
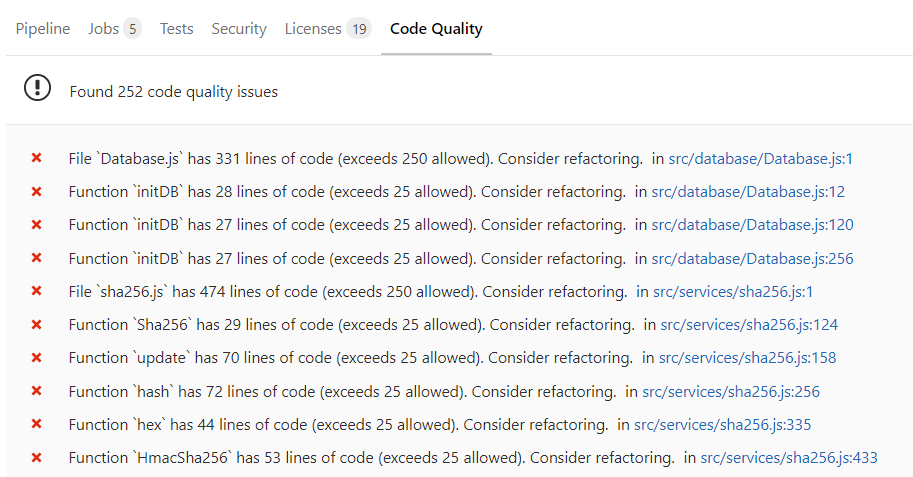
- Code quality tests to detect code parts that could be more ‘clean’ code
(It was also possible to run DAST and license tests but we left that aside at the moment)
We connected it to GitHub because the project keeps updating there – we actually connected directly to git repo.
In fact, we can say that we also made the app’s CI open source.
So what are the findings we found?
When we ran the apps’s CI pipeline on Saturday night, March 28
we found:
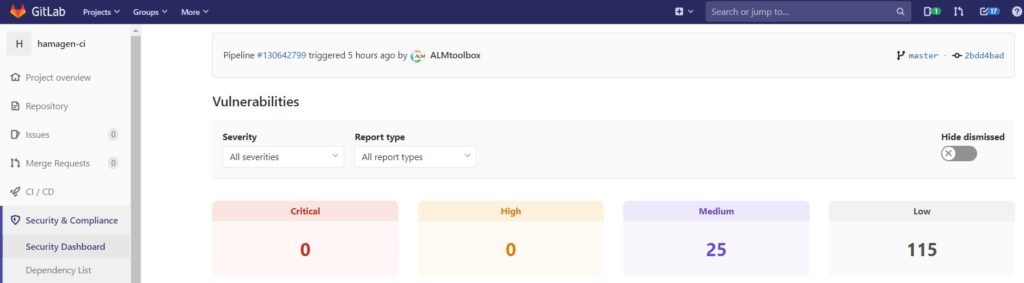
25 Medium Risk Vulnerabilities
115 at low risk:
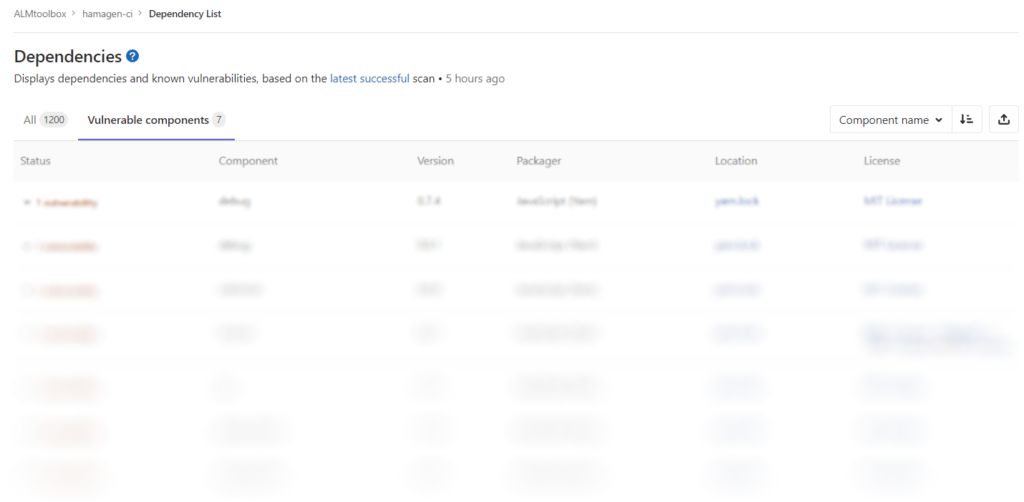
7 vulnerabilities were discovered in running dependency scanning:
About 10 vulnerabilities were found when running a static code test on the app code:
and about 250 code quality issues were found:
Of course, for information security reasons, we prefer not to disclose the results of the runner-up here publicly, we invite the project developers to contact us directly and we will create an account that will allow them to view everything in detail (including which file has which file and which line of code; Discovered and more) – and run the tests anytime they want – for the continuous improvement of the app. To get a user please email us at devops@almtoolbox.com.
We hope the CI we have built will be helpful – and invite anyone interested to look at the running settings and also offer suggestions for improvement.
The CIs we built (with the pipelines) for the app are available in the GitLab public cloud and can be viewed here:
https://gitlab.com/almtoolbox/hamagen-ci/pipelines
Suggestions for improvement are welcome at email devops@almtoolbox.com .
Special thanks: Alex Karnovsky (ALM-Toolbox) and Xiaogang Wen (GitLab Inc)
ALM-Toolbox company is a GitLab Premier Partner.
We have experts that can help you with the following:
- Plan a new GitLab implementation (cloud / on-premises / private cloud / “hybrid”)
- Align GitLab to in-house software development processes and flows
- We can help you with purchasing and saving costs on GitLab licenses
- Implement integration with JIRA, Jenkins, Slack, Artifactory, Kubernetes, Docker, ClearCase and other DevOps /ALM tools
- Customization and add-ons development
- GitLab and Git training
- Managed services
- Implement migration from Git, BitBucket, Jenkins, GitHub, ClearCase, RTC, TFS, SVN, JIRA and more
Contact us: gitlab@almtoolbox.com or 866-503-1471 (USA/Canada) or +972-722-405-222 (international)
Related Links:
- New app tells you when you’ve come in contact with a coronavirus patient (Jerusalem Post)
- The sound of coronavirus: Israeli apps helping contain pandemic
- Source code of “The Shield” application (GitHub)